Password hysteria
It seems to me that at least once every year, the password discussion boils up again. One fraction demands passwords to become increasingly complex and long, while the other is already overtaxed with remembering their present, simple passwords.
It's interesting that neither of these fractions actually know what they are talking about. What is a "good" password? How can I know for sure? And when do I need it?
Surely, that is a good password. Or is it? No, it isn't. First, never take passwords from the interwebs, even if they look as trustworthy as Steve Gibson's page, the well-known seller of snake oil. Second, the 63 characters offered there are much too long for purposes as a password — they are rather suitable as passphrase for wifi access (for this purpose, however, I recommend haui's scripts). As password, you can't possibly remember it.
Rule No. 1: You must be able to remember your password.
I'm really fed up with people forgetting their password. Resetting forgotten passwords easily amounts to 80% of the time I spent on my temporary admin job. I'm also fed up with people who have chosen a password which is so "difficult to type" that they need 12 min to complete the login process (try AltGr-H vs. AltGr-h).
Rule No. 2: Length is more important than "difficulty".
For maximum entropy, the complexity C of a password is simply given by the product of its length $\lambda$ with the binary logarithm of the character space $\Psi$:
$\mathcal{C} = \lambda \log_2(\Psi)$
The following diagrams visualize this relation:
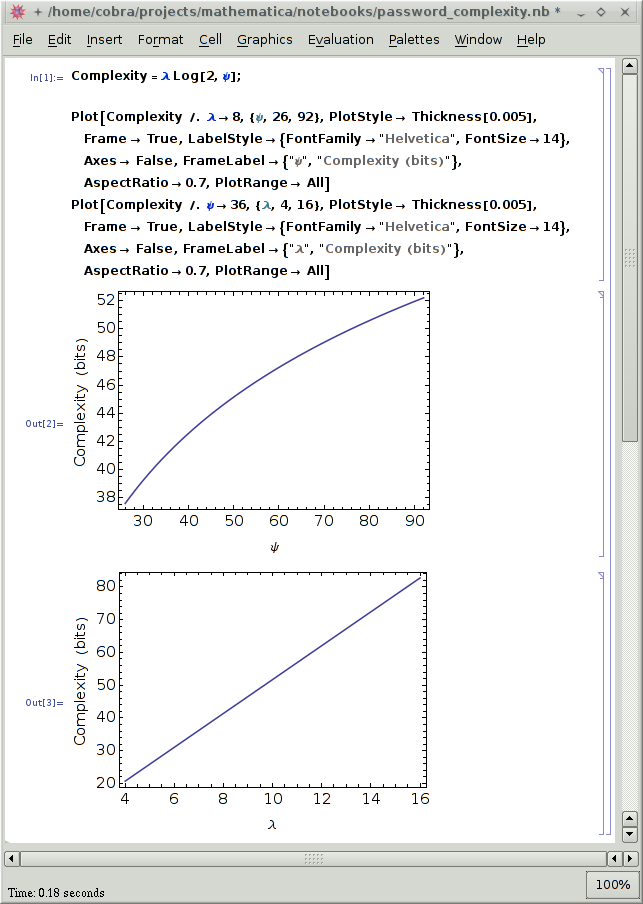
As you see, the complexity increases linearly with λ but sublinearly with ψ. Shouldn't this graph convince everybody to simply use longer passwords, instead of increasingly cryptic ones? Yes, it should, but a logarithm is a thing not understood by the common man politician.
Rule No. 3: Check your passwords
The security lobby wants you to believe that selecting a 'secure' password amounts to rocket science. Well...that is not entirely untrue. The simple method given by the equation above works only for the idealized case of maximum entropy. In reality, however, passwords do not have maximum entropy, and that affects their strength dramatically.
Stay away from intransparent password checkers such as those integrated into several applications (firefox, for example). A "password quality meter" in the form of a bar doesn't tell you anything.
John Walker wrote code to determine the entropy of a given string or file.
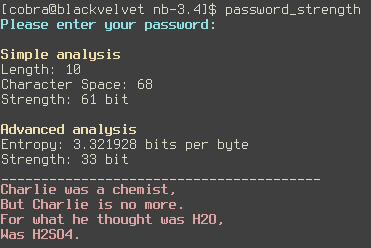
I've compiled a 64-bit version of John's program which you can find here. The bash script which created the above output is available here. The script performs a crude check for dictionary words, and then analyzes the supplied password (i) with the maximum entropy approximation (simple analysis), and (ii) with John's entropy code (advanced analysis).
For short passwords, the simple method vastly overestimates the actual complexity of the password. However, this overestimate may be relevant also for long passwords. Try 'aaaaaaaaaaaaaaaaaaa' as example.
You may also compare passwords such as '9g/<\_6?!>0' and 'HerrRasmussensAra'. Draw your own conclusions. 😉