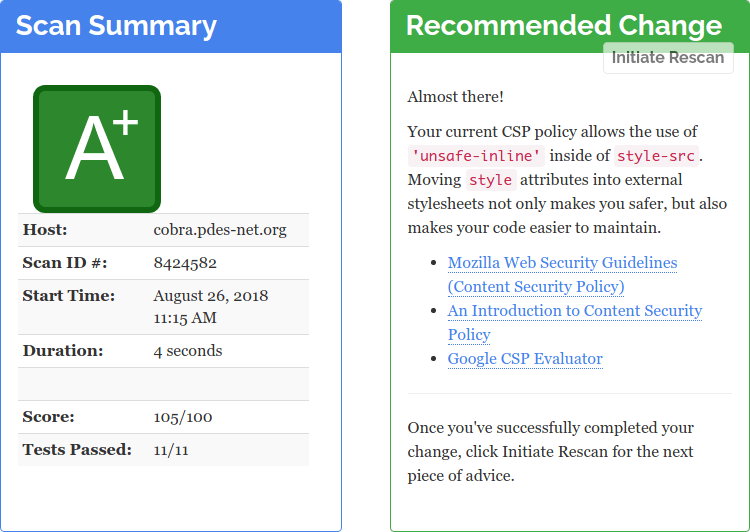
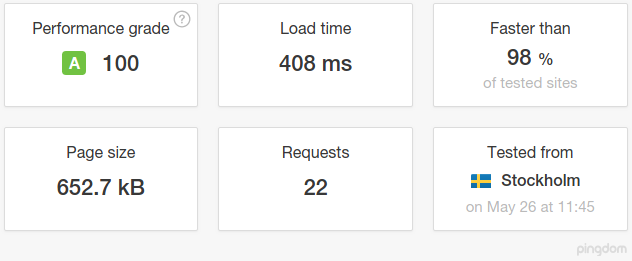
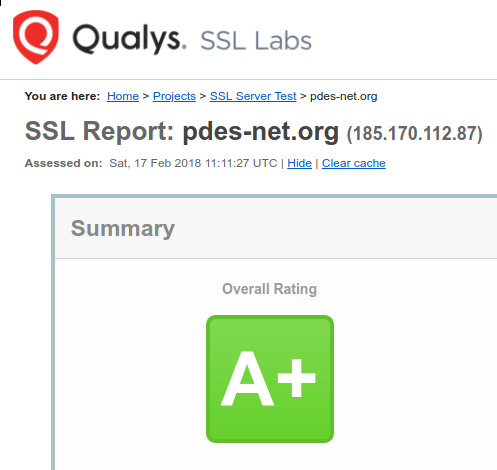
A reader of my previous post remarked that while he found my reminiscences amusing, he believes them to be factually incorrect. Windows and MacOS, he insists, are not prone to crashes as I've described, but are just as stable as any Linux.
That's more or less true, but only for times more recent than those I've dwelled on, namely, the times prior to the release of MacOS X and Windows XP in 2001 (and yes, I knew the older versions of NT and was impressed by their stability, but I didn't like their price tag!).
But if recent versions of MacOS and Windows do not exhibit any deficiency in terms of stability, the reader asks, is there any other reason to prefer Linux?
One? Well, let's at least briefly discuss some of the aspects that led me to chose Linux instead of Windows or MacOS. GNU/Linux is free software, both as in speech as in beer. Contrary to the free software foundation, I'm pragmatic enough to appreciate the latter point as least as much as the former one. Had I decided to employ commercial software for my work, I would not have been able to equip desktop, notebook, and netbook with the complete set of applications required for my work. As it is, I'm fully equipped to work at both office and home, at a pub, or while travelling, without the need to carry a high-end notebook back and forth between all of these locations. I greatly enjoy this freedom.
But free software is not a phenomenon restricted to Linux. In fact, almost everything I really need for my work on an everyday basis is available for Windows as well. So what's the difference?
The difference is the effort is takes to get everything working. On Windows, software installation hasn't changed since the 1990s. Software is installed from any installation medium deemed to be trustworthy by the user or, more recently, by Microsoft. In the 1990s, freeware was installed from CDs acquired at computer shops, nowadays, from any place in the internet. The user usually 'googles' for the software, opens the first hit without checking if it is the developers' site or some obscure download portal, downloads the installer, and installs it by clicking on various 'next' and 'yes' buttons without paying attention to the browser toolbars and other potentially unwanted utilities installed at the same time. The user repeats this awkward procedure for every software to be installed. And that's just the beginning: for the vast majority of both free and commercial software, the user has to check for updates himself, and if there is an update, he has to go again through the same archaic, error-prone, and time-consuming routine.
That's because the Microsoft updater only updates Windows and software from MIcrosoft (such as Office), but nothing else. This update is scheduled to occur only once per month (at the patch tuesday), but is so slow and heavy on resources that every Windows user dreads this day. No wonder Windows users hate updates – but it never ceases to surprise me that they don't draw the obvious conclusion. In particular since this situation is not a mere inconvenience, but inevitably results in unpatched systems that are easily compromised. With potentially unwanted consequences. 😉
The game-changing feature of Linux compared to its commercial rival(s) is the existence of central software repositories, containing tens of thousands of individual program packages, combined with a powerful built-in package management system. Updating the system updates every single program installed on it. Security updates are not held back but are delivered in time, typically even before you read about the underlying vulnerability in the news—at least when using the big six. And installing the updates is usually a matter of seconds to (at most) minutes and does not require a reboot (with the exception of libc and kernel updates).
But that's not the only advantage of the GNU/Linux software distribution model. For example, one can transform a vanilla Linux installation into a dedicated workstation within minutes, and I find that immensely useful. That's because I need a number of applications for my work, including texlive, libreoffice, gnuplot, numpy, scipy, matplotlib, mpmath, gmpy, sympy, pandas, seaborn, hyperspy, gimp, inkscape, scribus, gwyddion, imagej, vesta, and perhaps a few more. On Arch Linux, I'm able to install all of these packages with a single command that takes me a few seconds to enter. And from that moment on, all of these applications are included in the update process, and I get the most current version available automatically. On Windows, I would not only have to search for these programs on the internet, manually download the installation files, and install all programs individually, but I also would have to update all of this software by myself, without any kind of automatism. That means once again visiting the respective websites, downloading the new installation files, ...
Just the first time installation is the work of one day. Do you really think I want to continue doing that for the rest of my life? As a matter of fact, I don't, just as everybody else. And as a consequence, you'll find plenty of outdated software on your average Windows installation. This situation is arguably the major reason why Windows is the preferred target of malware developers: they can simply rely on the fact that their drones will find a huge number of vulnerable targets.
When I set up my wife's gaming rig, where Windows serves as a game starter, I've decided to install and update the few applications she needs with Ninite, and I'm not unhappy with this poor man's package manager. I've also installed Secunia's Personal Software Inspector to detect outstanding updates. Alas, this very useful tool has been discontinued, and I have to find a replacement. There are several contenders, but as usual under Windows, it is not clear which of them are trustworthy, in the sense that which of them are actually doing the job advertised, and not instead being a vehicle to deliver ads to your desktop. It takes time to separate the wheat from the chaff, time I could have otherwise spent on much more valuable and enjoyable activities. That's Windows, the greatest productivity killer ever invented.
Perhaps I should have a look at Chocolatey, which claims to be a “real” package manager for Windows (for a comparison with Ninite, see here). Now wouldn't that be the perfect tool for Windows, which is marketed since version 10 as a service receiving regular updates that contain new features and other changes? Sure it would, but what does Microsoft do with this chance to establish Windows as a rolling release model? They stick to the patchday and roll out new features in the form of semiannual 'Creator Updates', which turn out to require a full upgrade installation. Home users can't even delay this upgrade.
That's ... well, pathetic. In the end, Windows in 2020 will be no different from Windows in 1994: a pile of duct-taped debris desperately trying to look like a modern operating system.